Phishing Emails
Current Phishing Scams Reported at Forsyth Tech
REPORT phishing emails by using the "Report Message" feature in Outlook, see the guide below for information.
If you responded to a phishing email, contact the ITS Support Center immediately at https://its.forsythtech.edu or (866) 517-3567.

What is a Phishing Email?
Forsyth Tech, as well as many other large organizations, are under more information security attacks than ever before. One of the most common types of attacks are phishing email scams. Phishing email scams are attempts by scammers to trick you into giving out personal information such as your bank account numbers, passwords and credit card numbers.
Phishing email scams come in all shapes and sizes. The best phishing emails will copy the look and feel of the organization or company they are impersonating to the point it becomes very difficult to recognize.
Example:
Here is an example of a phishing email that recently circulated:
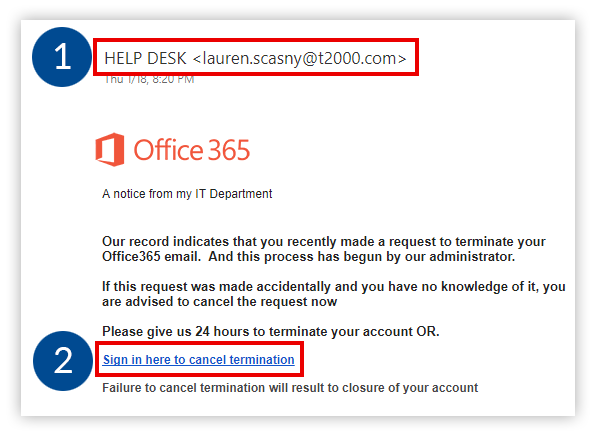
How to Spot Phishing Emails

Check the sender information:
The sender’s name is “HELP DESK”, however, the actual email address does not contain “@forsythtech.edu”. This is a red flag that this email is not coming from any department inside of Forsyth Tech.

Check links before clicking:
Whenever you see a link in an email, always hover your mouse of the link to view the actual website address of the link. If you do not recognize the website, then do not click the link.

Other indicators:
- May show the sender on behalf of someone and generally does not contain the sender's email.
- May not contain email signatures or any contact information.
- May contain bad grammar and capitalization errors.
- Generally require you to take quick action, such as verifying your account to prevent it from being deactivated
- Be particularly vigilant during holidays or during significant events since attackers heighten their activity during these times.
What to do if you get a phishing email
1. Send any phishing emails you receive to itssupport@forsythtech.edu.
- If you suspect it may be a phishing email, ITS Support can review the message and advise if it is legitimate or not.
- If you know it is a phishing email, ITS Support can take measure to have the phishing attack blocked.
2. Never respond to any email with confidential information. Forsyth Tech and other legitimate businesses will never ask for this information via email.
3. Use your mouse to hover over links in an email. This will show you the actual website you will be directed to if you click that link. It is always best to type the address into your web browser, rather than clicking a link in an email.
How to Protect Yourself
Here are some best practices that will help protect you and your information:
- Beware of messages that claim your account has been suspended
- Be suspicious of any email containing urgent requests for personal financial information
- Never click on a link in an email. Instead, always type the legitimate Web address of the site you want to reach directly into your Web browser.
- Be suspicious of email messages and other electronic communications from sources you do not know or recognize
- Use the latest versions of your operating system (OS) and applications
- Have the latest security software updates (patches) installed. This includes patches for your OS and applications
- Keep your anti-virus software up to date
- Report any suspicious emails